OUR NETWORK
Find our ATMs, Service-Centers, Cash Payment Terminals and other physical touchpoints on an interactive map


Protect your information assets from fraudulent schemes
Information security is one of the most pressing challenges of the modern world in recent years.
The technological progress of the last decades have greatly simplified the daily life of modern human.
Today, with the click of a finger on a smartphone, it is possible to send financial assets anywhere in the world and make real-time conference calls to foreign partners via video calling.
Growing at such an unprecedented rate, digital technologies, along with comfortable services, are opening up new opportunities for fraudsters who aim at gaining access to the personal information of others.
The recommendations on this page will help you protect yourself from fraudulent schemes. By following the tips, you will significantly reduce the risk of unauthorized disclosure of your personal information, and in case of occurring of such an event, you will be prepared to respond appropriately.
If fraudsters have gained access to your or someone else's information, please call us immediately: 0322555500
Briefly about Internet Security Rules:
Briefly about Internet Security Rules:
When creating a secure password, you may consider the following recommendations:
It is also recommended to include at least one special symbol (! @ # $ % ^ & * ( ) { } [ ])
Criminals often conduct research on their target, resulting in mastering our data: first name, last name, date of birth, personal number. . . Therefore, in order to increase the level of security, our password / code word should not be connected with our personal information / life.
Smartphone Security - Follow the safety rules on personal smartphones. This will also protect your personal information better.
Please be aware of:
Today, literally every day, millions of phishing emails are sent from various addresses to gain access to our personal information.
To protect yourself, we recommend:
Email can be likened to a real one
At first glance, it is virtually impossible to detect an error, but after observing we can detect the address is created by the wrong / criminal "Name@Examp1e.com" where the letter "L" is replaced by the number "1".
Phishing is a fake email that looks trustworthy and is intended to mislead the user and steal information or hack into a computer.
Such letters are characterized by job, attractive, uplifting or scandalous titles. For example:
Often in similar emails you are asked to go to the specified link or website, however the links are actually malicious and by going through it the computer will be infected.
Detecting similar links is quite simple - hover the mouse pointer over the link and pause for a moment, after which the system will show the real address:
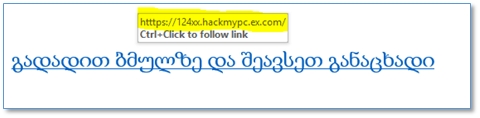
Similar URLs often contain numbers, incorrect names (e.g. Example and not Example) and have odd suffixes (ex.com, ucoz.net, install? = Ex, etc.).
Phishing emails may also contain attachments containing malicious software, and malicious software may be embedded in Word, Excel, Power Point, and PDF files.
Secure Sites - When using the Internet, information is exchanged between us and the web resource. The information transmitted may include: user and password, card information, personal number and other personal and confidential information.
To ensure the security of the transmitted information, pay attention to the website address and the certificate used.
The website address should start with the https prefix and not http.
Https means that the information exchanged between us and the website is encrypted with a special certificate. Typically, HTTPS (protected) websites have a padlock in the address bar.